Microsoft Defender Antivirus: It’s the built-in security software on your Windows machine, but is it actually any good? Forget the boring textbook definition; let’s dive into whether this free antivirus is a lifesaver or just taking up space. We’ll explore its features, compare it to the big dogs like Norton, and see if it truly holds up against modern malware threats.
Plus, we’ll tackle the real questions: Is it resource-hungry? Does it actually protect your privacy? Get ready for a no-nonsense look at Microsoft Defender.
This guide breaks down everything you need to know about Microsoft Defender Antivirus, from its core functionalities and system requirements to its performance impact and comparison with other antivirus solutions. We’ll cover installation, troubleshooting, and even delve into the often-overlooked aspects of privacy and data handling. By the end, you’ll have a clear understanding of whether Microsoft Defender is the right choice for your digital security needs.
Microsoft Defender Antivirus Features
Microsoft Defender Antivirus, formerly known as Windows Defender, is the built-in antivirus solution for Windows operating systems. It’s a solid, free option that provides a surprising amount of protection for the average user, though power users might want to consider supplementing it with additional security measures. This section will explore its core features and how they work to keep your system safe.
Defender’s core functionality centers around real-time protection, scanning for malware, and providing a layer of security against online threats. It’s designed to be unobtrusive, working in the background to keep your system secure without bogging down performance.
Protection Layers in Microsoft Defender Antivirus
Microsoft Defender employs multiple layers of protection to defend against a wide range of threats. These layers work together to create a robust security system. A single point of failure is less likely with this layered approach, offering better protection than a single security method.
These layers include real-time protection, which constantly monitors your system for malicious activity; a cloud-based protection system that leverages Microsoft’s vast network to identify and analyze new threats; and a behavioral monitoring system that watches for suspicious activities even from unknown files. Finally, it also offers a firewall to control network traffic and prevent unauthorized access to your system.
Real-Time Protection in Microsoft Defender
Real-time protection is the backbone of Microsoft Defender’s security. It constantly monitors files and processes as they are accessed or executed on your system. When a potentially malicious file is detected, Defender uses a combination of signature-based detection (comparing the file to a database of known malware) and heuristic analysis (analyzing the file’s behavior) to determine if it’s a threat.
If a threat is identified, Defender will take action, such as quarantining or deleting the file, notifying the user, and providing remediation options. This constant vigilance is crucial in preventing infections before they can cause damage.
Feature Comparison: Microsoft Defender vs. Norton
The following table compares key features of Microsoft Defender and Norton 360, a popular third-party antivirus solution. Note that feature sets and pricing can change, so this is a snapshot of what’s offered at the time of writing. Always check the latest information from the vendors.
| Feature | Microsoft Defender | Norton 360 | Comparison |
|---|---|---|---|
| Real-time Protection | Yes, signature-based and heuristic analysis | Yes, with advanced threat detection | Both offer real-time protection, but Norton typically boasts more advanced features like machine learning for threat identification. |
| Virus Scanning | On-demand and scheduled scans available | On-demand, scheduled, and proactive scans; more scan options | Both provide scanning capabilities, but Norton generally offers more granular control and options. |
| Firewall | Built-in Windows Firewall | Included, often with more advanced features and customization | Defender uses the Windows Firewall; Norton provides a potentially more feature-rich firewall. |
| VPN | No | Included in higher-tier plans | Norton offers a VPN as an added security layer, a feature absent in the free Defender. |
| Parental Controls | No | Included in some plans | Another feature offered by Norton but not Defender. |
| Cost | Free (included with Windows) | Subscription-based, varying in price depending on features | Defender is a free option; Norton requires a paid subscription for its full feature set. |
System Requirements and Compatibility

Microsoft Defender Antivirus, while generally lightweight, still needs sufficient system resources to run effectively and provide optimal protection. Understanding its system requirements ensures smooth operation and prevents potential performance issues. This section details the minimum and recommended specs, compatibility across various Windows versions, and any hardware considerations.Knowing your system’s capabilities is key to getting the most out of your antivirus.
Insufficient resources can lead to slower scans, delayed updates, and even reduced protection. Let’s dive into the specifics to ensure you’re running Defender at its best.
Minimum and Recommended System Requirements
Microsoft doesn’t publish rigidly defined “minimum” and “recommended” specs in the traditional sense. Instead, the performance of Defender is highly dependent on the overall system’s capabilities. A system that’s already struggling with other applications might find Defender’s resource usage more noticeable. However, a modern system with at least 4GB of RAM and a reasonably fast processor will generally experience no issues.
More RAM and a faster processor will, of course, result in quicker scan times and smoother overall operation. Consider your typical computer usage; if you’re running resource-intensive applications simultaneously, allocating more RAM to your system would be beneficial.
Windows Operating System Compatibility
Microsoft Defender Antivirus is tightly integrated with the Windows operating system. It’s essentially a built-in component, so compatibility is largely determined by the Windows version itself. While it’s designed to work seamlessly with most recent versions, older systems might lack certain features or experience performance limitations.
Hardware Limitations and Considerations
Defender’s impact on hardware is generally minimal. The primary resource demands are CPU cycles (for scanning) and RAM (for holding data during scans and updates). Older hardware with limited RAM or slower processors might experience noticeable performance impacts during intensive tasks like full system scans. However, Defender is designed to be efficient, so even on older systems, it should still function adequately.
Consider regularly clearing temporary files and unnecessary programs to optimize system performance, further reducing any potential strain caused by Defender.
Supported Windows Versions
The following list shows the currently supported versions of Windows. Microsoft regularly updates this list, so it’s always best to check the official Microsoft website for the most up-to-date information.
- Windows 11
- Windows 10 (versions 20H2 and later)
- Windows Server 2022
- Windows Server 2019
Installation and Setup Process
Getting Microsoft Defender Antivirus up and running is pretty straightforward, especially if you’re using a Windows machine. It’s usually built-in, so you might not even need to do much! But there are a few things to know about the process, initial settings, and keeping it updated.
The installation and setup of Microsoft Defender Antivirus varies slightly depending on your Windows version and whether it was pre-installed. On newer Windows versions, it’s usually already active and ready to go. For older systems, or if you’ve disabled it, you might need to do a bit more.
Installation on a New System, Microsoft defender antivirus
For a brand-new Windows installation, Defender is typically enabled by default. You’ll likely see a notification about it during the initial setup process. After Windows finishes installing, Defender should automatically start its initial scan in the background. You can find it in the system settings under “Windows Security” or by searching for “Virus & threat protection”. No extra downloads or installations are needed; it’s all integrated.
Initial Configuration Options
Once Defender is running, you can customize several settings to fit your needs. This includes toggling real-time protection on or off (generally, you’ll want this ON!), scheduling scans (daily, weekly, or custom), and managing exclusions (telling Defender to ignore specific files or folders). You can also adjust the level of notification you receive. You might want to be notified about every single suspicious file, or only about critical threats.
It’s totally up to you.
Updating Antivirus Definitions
Keeping your antivirus definitions up-to-date is crucial for effective protection. Defender usually updates automatically in the background, but you can manually check for updates. This ensures that Defender has the latest information on the newest viruses and malware, allowing it to identify and neutralize threats more effectively. To do this, simply open Windows Security, navigate to “Virus & threat protection”, and click “Virus & threat protection updates”.
Click “Check for updates” to initiate the process. It’s a good habit to check this periodically, even if automatic updates are enabled.
Step-by-Step Guide for Installation on a New System
While typically automatic, here’s a step-by-step guide for ensuring Defender is properly enabled and running on a fresh Windows install:
- Complete the Windows installation process. This includes setting up your user account and any initial preferences.
- After setup, Windows will likely automatically start Defender. You may see a notification or it might run silently in the background.
- Open the Windows Security app (search for “Windows Security” in the start menu).
- Navigate to “Virus & threat protection”.
- Verify that real-time protection is turned “On”.
- Perform a quick scan to check for any potential threats. (This is optional but recommended).
- Check for updates to ensure you have the latest virus definitions. (As described above).
Performance Impact on System Resources

Microsoft Defender Antivirus, while generally efficient, does consume system resources during scans and other operations. The impact varies depending on factors like the size of your hard drive, the amount of data being scanned, and the power of your computer’s processor and RAM. Understanding this impact helps manage expectations and optimize your system for peak performance.
Resource usage during scans and other antivirus activities is dynamic. A full system scan, for example, will naturally consume more CPU and memory than a quick scan of only recently downloaded files. Disk I/O (input/output) will also increase significantly during scans as the antivirus engine reads and analyzes files. This increased activity can lead to a noticeable slowdown in other applications, especially during intensive tasks like video editing or gaming.
CPU and Memory Usage During a Full System Scan
A full system scan demands significant processing power. The CPU usage will spike considerably, often reaching 70-90% depending on your system’s specs and the size of your hard drive. Similarly, memory consumption will increase, potentially impacting the performance of other running applications. The duration of this high resource usage depends on the size of your hard drive and the speed of your system.
A larger hard drive with more files will naturally take longer to scan.
The following chart illustrates a hypothetical scenario of CPU and Memory usage during a full system scan. Note that this is a generalized representation and actual usage will vary based on individual system configurations and the specific files being scanned.
Hypothetical CPU and Memory Usage During a Full System Scan
Imagine a bar chart. The X-axis represents time (in minutes), progressing from 0 to
60. The Y-axis represents percentage usage (0% to 100%). Two lines are graphed: one for CPU usage and one for memory usage. Both lines start at around 10-15% baseline usage.
At the beginning of the scan (around minute 0-5), both lines show a rapid increase, peaking at approximately 85% for CPU and 65% for memory around minute 15-20. After the peak, the lines gradually decline, settling back to around 10-15% by minute 60 (the end of the scan). The CPU line might fluctuate more dramatically than the memory line due to the nature of disk I/O operations.
The shape of both curves is roughly bell-shaped, reflecting the intensity of the scan.
Comparison to Other Antivirus Solutions
While direct comparisons are difficult without controlled testing environments and identical hardware, general observations suggest that Microsoft Defender performs reasonably well compared to other reputable antivirus solutions. Some third-party solutions might boast slightly lower resource consumption during scans, but this often comes with trade-offs in detection rates or features. The performance impact is typically manageable for most users, though users with lower-spec systems might experience more noticeable slowdowns.
Many users report little to no perceptible impact during normal usage, even with real-time protection enabled.
Disk I/O Impact During Scans
The increased disk I/O during a full system scan can lead to noticeable delays in other disk-intensive operations. For example, loading large files, saving documents, or installing software may take longer while a scan is in progress. The extent of this impact depends on your hard drive’s speed (SSD vs. HDD) and the number of concurrent processes. Solid-state drives (SSDs) generally exhibit less performance degradation than traditional hard disk drives (HDDs) due to their faster read/write speeds.
Protection Against Malware Types
Microsoft Defender Antivirus boasts a robust defense against a wide array of malware threats, constantly evolving to stay ahead of the curve. It employs multiple layers of protection, combining signature-based detection with advanced heuristics and machine learning to identify and neutralize even the most sophisticated attacks. This multifaceted approach ensures comprehensive protection across various malware categories.Microsoft Defender effectively protects against a broad spectrum of malware, including viruses, worms, trojans, ransomware, spyware, adware, and rootkits.
These threats vary significantly in their methods of infection and their impact on a system, requiring a diverse and adaptable security solution. The software’s ability to handle these threats is a key component of its overall effectiveness.
Malware Families and Detection Methods
Defender utilizes a combination of techniques to identify and neutralize malware. Signature-based detection involves comparing malware code against a vast database of known malicious signatures. Heuristic analysis examines the behavior of a program to identify suspicious activities, even if the code itself is unknown. Machine learning algorithms analyze vast datasets of malware samples to identify patterns and predict future threats.
For example, the WannaCry ransomware attack, which leveraged an exploit in older versions of Windows, would be detected through signature-based methods once its signature was identified and added to the database. More sophisticated, zero-day exploits, however, might be initially detected through behavioral analysis, flagging unusual network activity or file encryption attempts. The polymorphic nature of some malware, where the code changes to evade signature-based detection, is countered by the heuristic and machine learning components of Defender.
Threat Level Handling
Microsoft Defender categorizes threats based on their severity and potential impact. Low-level threats might be minor annoyances like adware, while high-level threats represent significant risks, such as ransomware capable of encrypting critical files or data exfiltration attempts. Defender’s response varies accordingly; low-level threats might simply be quarantined, while high-level threats trigger immediate actions, such as blocking execution and initiating a full system scan.
The software also provides users with varying levels of control over how it responds to different threat levels, allowing customization to suit individual needs and risk tolerance.
Malware Types and Defender Response
| Malware Type | Defender Response | Example |
|---|---|---|
| Virus | Quarantine, removal, system scan | Stuxnet (a sophisticated worm targeting industrial control systems, though Defender’s response would be based on its current signature database) |
| Worm | Network isolation, removal, system scan | Conficker (a worm that spread rapidly through network vulnerabilities) |
| Trojan | Quarantine, removal, system scan | Emotet (a trojan known for its banking malware capabilities) |
| Ransomware | Block execution, quarantine, attempt file recovery (if possible), system scan | Ryuk (a ransomware variant known for its aggressive encryption techniques) |
| Spyware | Removal, privacy settings adjustments, system scan | Many variations exist, often bundled with other software |
| Adware | Removal, browser cleanup, system scan | Various adware programs that display unwanted advertisements |
| Rootkit | Deep system scan, removal, potential system restore | Sophisticated rootkits designed to hide malicious processes |
User Interface and Experience
Microsoft Defender Antivirus boasts a relatively straightforward and clean user interface, aiming for simplicity rather than overwhelming users with complex settings. Its design prioritizes ease of access to key security features while minimizing clutter. This approach makes it user-friendly across a range of technical skill levels, from novice to expert.The interface is primarily composed of visual cues and concise textual descriptions, reducing the reliance on extensive tooltips or help menus.
This design choice contributes to a quicker learning curve and a more intuitive experience for most users.
Ease of Use and Navigation
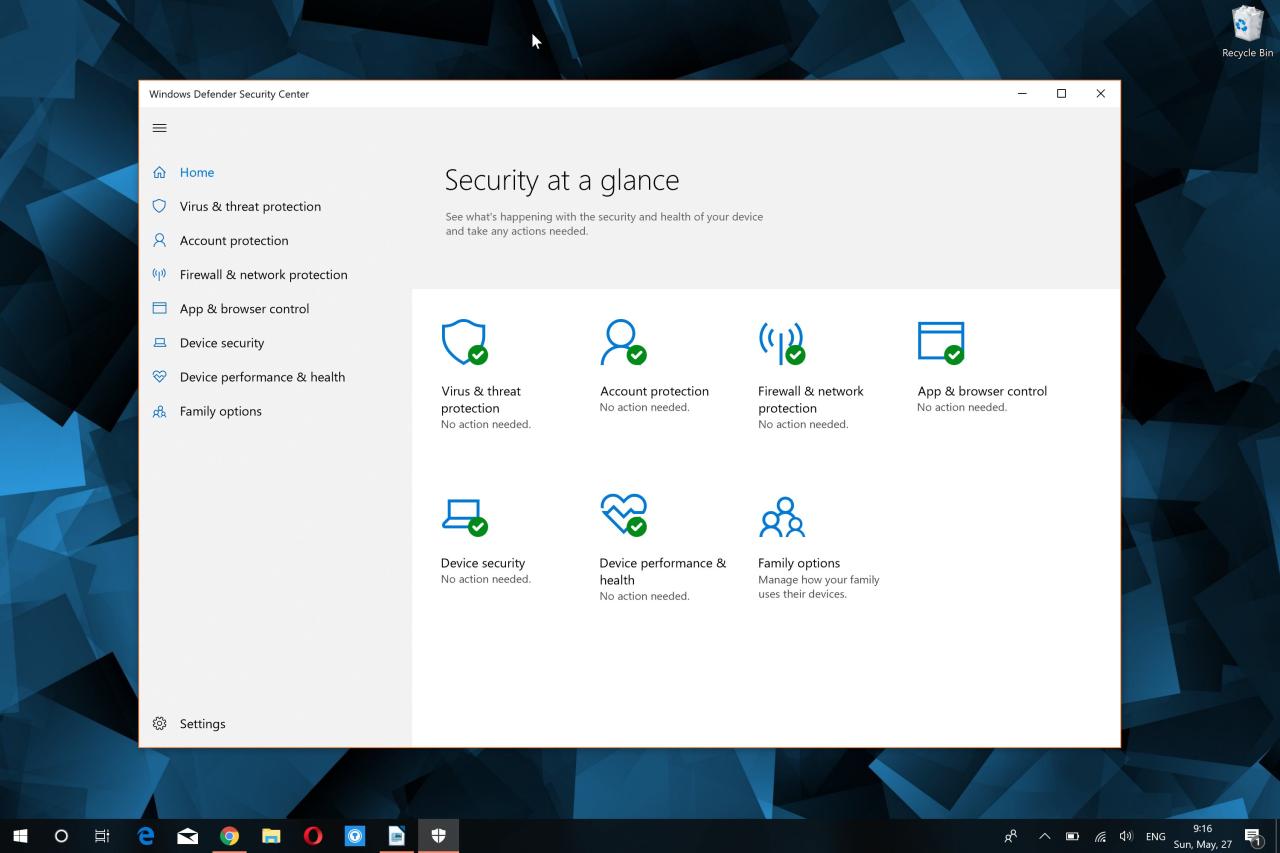
The main dashboard presents a clear summary of the system’s security status, highlighting any potential threats or issues requiring immediate attention. Navigation through the different sections, such as virus & threat protection, account protection, and app & browser control, is intuitive and generally requires only a few clicks. Even users unfamiliar with antivirus software should find it easy to understand the basic functionality and status of their protection.
For more advanced users, access to detailed settings and configurations is readily available, though it’s well-organized to avoid overwhelming those who prefer a simpler experience.
Accessibility Features
While Microsoft doesn’t explicitly list extensive accessibility features for Defender Antivirus on their support pages, the general design principles of clear visual cues, concise text, and straightforward navigation contribute to accessibility for many users with disabilities. The interface is generally compatible with screen readers and keyboard navigation, although specific certifications or detailed accessibility statements are not publicly available. The reliance on visual indicators rather than complex layouts assists users with visual impairments who may rely on screen readers for information.
Main Dashboard Components
The Defender Antivirus main dashboard typically displays a concise summary of the system’s security status. Key components usually include: a quick overview of the protection status (e.g., “Up to date,” “Threats detected”), a quick access button to initiate a scan, a notification area displaying any active threats or alerts, links to access more detailed settings and reports, and a quick access to the account protection settings (for features like Microsoft Family Safety).
The dashboard is designed to provide a quick assessment of the system’s security, allowing users to quickly identify and address any potential issues.
Security Features Beyond Antivirus: Microsoft Defender Antivirus
Microsoft Defender isn’t just your average antivirus; it’s a comprehensive security suite designed to protect your Windows system from a wide range of threats. Beyond its robust antivirus capabilities, it boasts several additional features that work together to create a multi-layered defense system. These features go beyond simply detecting and removing malware; they actively prevent attacks and protect your sensitive data.
These extra layers of protection are crucial in today’s increasingly sophisticated threat landscape. Cybercriminals are constantly developing new ways to bypass traditional antivirus, so having a suite of proactive defenses is essential for maintaining robust security. Microsoft Defender’s integrated approach combines real-time protection with proactive threat detection and prevention, making it a powerful tool for safeguarding your digital life.
Ransomware Protection
Ransomware is a serious threat, encrypting your files and demanding a ransom for their release. Microsoft Defender’s ransomware protection employs several techniques to mitigate this risk. Controlled folder access restricts unauthorized programs from modifying files in protected folders, effectively preventing ransomware from encrypting your important documents and pictures. This feature is highly configurable, allowing you to specify which folders are protected and which applications have access.
Additionally, Defender uses behavioral monitoring to detect suspicious activity indicative of ransomware, such as unusual file encryption patterns, and takes action to neutralize the threat before it can cause significant damage. The system also incorporates machine learning to improve its ability to identify and block new and evolving ransomware variants.
Cloud-Based Protection
Microsoft Defender leverages the power of the cloud to enhance its protection capabilities. This cloud-based protection provides several key advantages. First, it allows for faster threat detection and response. The cloud service constantly updates its threat intelligence database, enabling Defender to identify and respond to new threats almost immediately. Second, it enhances the accuracy of threat detection by analyzing data from millions of devices globally, identifying patterns and anomalies that might be missed by local analysis alone.
Finally, cloud-based protection provides access to advanced threat analysis and mitigation techniques that would be impractical or impossible to implement locally. This collaborative approach ensures that your system benefits from the collective intelligence of the entire Defender ecosystem.
Additional Security Features
Beyond ransomware protection and cloud-based features, Microsoft Defender offers a range of other valuable security tools. These features work in concert to provide a comprehensive security posture.
- Firewall: A built-in firewall controls network traffic, blocking malicious connections and preventing unauthorized access to your system.
- Exploit Protection: This feature mitigates the risk of software vulnerabilities being exploited by attackers. It works by applying various mitigation techniques to reduce the attack surface of your system.
- Attack Surface Reduction (ASR): ASR rules help prevent malicious applications from executing and spreading. It leverages heuristics and known malicious techniques to block potentially harmful actions.
- Tamper Protection: This feature prevents malicious actors from disabling or modifying important security settings, ensuring that your protection remains active and effective.
- Windows Security App: The central management hub for all of these security features, allowing users to easily monitor their security status and adjust settings.
Troubleshooting Common Issues
So, you’re running into some snags with Microsoft Defender? Don’t worry, it happens to the best of us. This section covers some common problems and how to fix them, saving you the headache (and maybe even a few frantic Google searches). We’ll walk through interpreting error messages and logs, and provide step-by-step solutions to get things back on track.
Many issues stem from simple misunderstandings or minor configuration problems. Others might indicate a more serious threat, so it’s crucial to understand how to diagnose the problem and take appropriate action. This guide will help you navigate those tricky situations.
Defender Not Running or Disabled
Defender might be accidentally disabled or encountering a conflict with other security software. Check your Windows Security settings (search for it in the start menu) to verify that Real-time protection is turned on. If it’s off, simply toggle the switch to “On.” If you’re using another antivirus program, uninstall it completely before relying solely on Defender. Sometimes, remnants of the old program can interfere with Defender’s functionality.
A restart after making these changes is usually a good idea.
High CPU or Disk Usage
High resource usage by Defender often points to a scan in progress, particularly a full system scan which can be resource intensive. Check the Windows Security interface; you should see the current status of any scans. If a scan is underway, simply wait for it to complete. If high resource usage persistsafter* a scan, a malware infection could be the culprit.
Run a full scan again, and if the problem continues, consider a system restore to a point before the issue started.
For example, imagine your CPU is pegged at 100% even when idle. This is unusual and suggests a problem. A full scan, followed by a system restore if necessary, can help pinpoint and resolve the issue. Remember to save your work before initiating a system restore!
False Positives
Defender, like any antivirus, isn’t perfect and can sometimes flag harmless files as threats. If a file or program you trust is quarantined, you can usually restore it from the quarantined items section within the Windows Security app. Before doing so, carefully consider the source and reputation of the file. If you’re still unsure, you can always search online for information about the flagged file to confirm its safety.
Interpreting Error Messages and Logs
Error messages from Defender often provide clues about the problem. Pay close attention to the error code (if provided), and search for it online. Microsoft’s support website is a great resource. Defender also keeps logs, which can provide more detailed information. You can access these logs through advanced settings within the Windows Security app, although interpreting them may require some technical expertise.
Look for patterns in timestamps and error codes to help pinpoint the cause.
For example, an error code might indicate a problem accessing a specific file or directory. This could be due to permissions issues or a corrupted file. The logs may further detail the file location and the specific error encountered.
Troubleshooting High CPU Usage (Step-by-Step)
- Check for active scans: Open Windows Security and look for any ongoing scans. If a scan is running, wait for it to finish.
- Check for other resource-intensive processes: Use Task Manager (Ctrl+Shift+Esc) to identify other applications consuming significant CPU resources. Closing unnecessary programs can free up resources.
- Run a full scan: Initiate a full scan with Defender to detect and remove any malware that might be causing the high CPU usage.
- Restart your computer: A simple restart can often resolve temporary glitches that are impacting resource usage.
- Check for driver updates: Outdated drivers can sometimes conflict with Defender and cause high CPU usage. Check your device manufacturer’s website for updated drivers.
- System Restore: If the problem persists, consider restoring your system to a previous point in time before the high CPU usage began.
Comparison with Other Security Suites
Choosing the right antivirus solution can feel overwhelming, given the sheer number of options available. Microsoft Defender, while built-in and free, often gets compared to comprehensive security suites offered by companies like Norton, McAfee, Bitdefender, and Kaspersky. This comparison will highlight the strengths and weaknesses of each approach, helping you determine which best suits your needs and budget.
Feature Comparison of Security Suites
The following table summarizes key features and pricing for several popular security suites, including Microsoft Defender. Keep in mind that pricing and features can change, so always check the vendor’s website for the most up-to-date information. Note that Microsoft Defender’s pricing reflects the fact it’s included with Windows. Other suites typically offer tiered pricing with varying levels of features and protection.
| Feature | Microsoft Defender | Norton 360 | McAfee Total Protection | Bitdefender Total Security | Kaspersky Total Security |
|---|---|---|---|---|---|
| Antivirus Protection | Yes | Yes | Yes | Yes | Yes |
| Firewall | Yes | Yes | Yes | Yes | Yes |
| VPN | No | Yes (limited data) | Yes (limited data) | Yes | Yes |
| Password Manager | No | Yes | Yes | Yes | Yes |
| Parental Controls | Limited (Windows Family Safety) | Yes | Yes | Yes | Yes |
| Identity Theft Protection | No | Yes | Yes | Yes (some plans) | Yes |
| Price (Annual, approx.) | $0 (included with Windows) | $100+ | $100+ | $100+ | $100+ |
Advantages and Disadvantages of Different Approaches
Microsoft Defender offers a solid baseline of protection at no extra cost. Its advantage lies in its seamless integration with Windows and its generally low impact on system performance. However, it lacks many advanced features found in comprehensive security suites. For instance, it doesn’t include a VPN, password manager, or robust parental controls.Comprehensive security suites like Norton 360, McAfee Total Protection, Bitdefender Total Security, and Kaspersky Total Security offer a broader range of features beyond basic antivirus protection.
These features can provide additional layers of security and convenience, but they come at a price. A disadvantage is the potential for performance impact, particularly on older or less powerful systems, and the added complexity of managing multiple features.
Scenarios for Solution Preference
For budget-conscious users with relatively low risk profiles, Microsoft Defender provides adequate protection. However, users who require advanced features like a VPN, password manager, or robust parental controls, or who have higher security needs due to online banking, online shopping, or frequent use of public Wi-Fi, will likely benefit from a comprehensive security suite. Similarly, businesses with stricter security requirements would likely choose a more robust, enterprise-grade solution.
Microsoft Defender is pretty solid, but sometimes your system needs a little extra oomph. If you’re noticing sluggish performance, grabbing a copy of CCleaner via ccleaner download might help clear out junk files and free up some space. After that cleanup, Defender should run even smoother, keeping your system safe and speedy.
For example, a small business owner handling sensitive financial data might opt for a paid suite with advanced features like data encryption and anti-phishing tools, whereas a casual home user might find Defender perfectly sufficient.
Privacy Implications and Data Handling
Microsoft Defender, like any antivirus software, collects some user data to function effectively and improve its services. Understanding how this data is handled is crucial for maintaining your digital privacy. This section Artikels Microsoft’s approach to data collection, usage, security, and transparency.Microsoft Defender’s data handling practices are governed by Microsoft’s privacy policy, which is readily available on their website.
The policy details what data is collected, why it’s collected, how it’s used, and with whom it’s shared. This includes information about the type of threats detected, the operating system version, and sometimes, anonymized system diagnostic information. It’s important to note that this data is primarily used to improve the software’s effectiveness and protect users from malware.
Data Collection and Usage
Microsoft collects data to enhance Defender’s capabilities and provide a more secure user experience. This data is used for threat detection, updates, and performance analysis. For example, data on detected malware helps Microsoft’s researchers understand emerging threats and develop more effective defenses. Anonymized diagnostic data contributes to overall product improvement, ensuring the software remains efficient and effective for all users.
The policy clearly states that personally identifiable information is only collected with explicit user consent or when required for security purposes.
Data Security Measures
Microsoft employs various security measures to protect user data from unauthorized access, use, or disclosure. These measures include data encryption both in transit and at rest, access controls limiting who can view and modify data, and regular security audits to identify and address vulnerabilities. Microsoft also uses advanced security technologies to detect and prevent potential breaches. The company’s commitment to security is demonstrated through its extensive investment in cybersecurity infrastructure and its proactive approach to threat mitigation.
Transparency of Data Handling Practices
Microsoft strives for transparency in its data handling practices. The privacy policy is readily accessible and written in clear, understandable language. Users can find detailed information about the types of data collected, the purposes of data collection, and how their data is protected. Microsoft also provides users with tools and settings to manage their privacy preferences, allowing them to control the amount of data shared with Microsoft.
This includes options to disable certain data collection features if desired. Regular updates to the privacy policy ensure users are always informed of any changes in data handling practices.
Summary

So, is Microsoft Defender Antivirus good enough? The answer, like most things in life, is: it depends. For everyday users who aren’t constantly clicking on sketchy links or downloading questionable files, it provides a surprisingly robust level of protection. Its integration with Windows is seamless, and it’s a solid free option. However, power users or those who handle sensitive data might want to consider a more comprehensive, paid suite.
Ultimately, understanding its strengths and limitations empowers you to make the best choice for your digital security posture. Now go forth and conquer those digital threats!
Questions Often Asked
Is Microsoft Defender Antivirus enough protection for gaming PCs?
Generally, yes, for casual gaming. However, intensive gaming often involves downloading mods and other potentially risky files, so a more robust solution might be preferable for hardcore gamers.
Can I disable Microsoft Defender temporarily?
Yes, but it’s generally not recommended unless you’re absolutely sure of what you’re doing and only for a very short time. Your system is vulnerable without real-time protection.
How much storage space does Microsoft Defender use?
Its footprint is relatively small, typically using only a few gigabytes of storage, but this can fluctuate based on updates and stored threat data.
Does Microsoft Defender slow down my computer?
It should have minimal impact on performance for most users. However, full system scans can temporarily slow things down. If you experience significant slowdowns, check for resource conflicts.
What happens if Microsoft Defender detects a threat?
It will quarantine or remove the threat. You’ll usually receive a notification, and you can review the details in the Defender app.